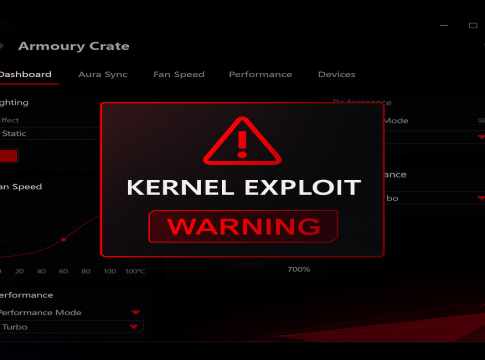
ASUS Armoury Crate: RGB Dreams Derailed by Security Nightmares
When it comes to RGB lighting solutions, ASUS’s Armoury Crate is often seen as a go-to option for gamers and tech enthusiasts alike. However, recent revelations have cast a long shadow over this flashy software, uncovering a critical security vulnerability that could pose significant risks to users.
What’s the Issue?
The flaw in question is known as CVE-2025-3464, identified by security researcher Marcin “Icewall” Noga from Cisco Talos. Scoring a hefty CVSS 8.8, this vulnerability lies within the driver component known as AsIO3.sys, which operates at kernel level—the heart of your operating system. Such deep access is troubling, especially when a failure happens.
The Nature of the Threat
This vulnerability emerges from a classic “time-of-check to time-of-use” (ToC-ToU) race condition. Essentially, Armoury Crate bypasses Windows’ robust security protocols like Access Control Lists (ACLs) and directly relies on its own internal mechanisms—namely, a hard-coded SHA-256 checksum for a specific executable, AsusCertService.exe. This means that an attacker can exploit this weakness with some clever trickery, such as creating malicious links that masquerade as legitimate files, ultimately gaining SYSTEM rights—unfettered access to memory and kernel functions.
Who’s Affected and How Bad Is It?
Worryingly, this vulnerability impacts all versions of Armoury Crate from 5.9.9.0 to 6.1.18.0, which covers a large user base. While attackers need local access to exploit this vulnerability, the increasing prevalence of social engineering tactics makes this a more pressing concern. Though ASUS was informed about the issue back in February, there’s currently no evidence of real-world exploitation. However, given the allure of kernel exploits for cybercriminals, this could quickly change.
What to Do Next?
For those using Armoury Crate, ASUS advises updating to the latest version through the application itself. However, users may be left pondering a broader question: does RGB lighting really need such elevated system permissions? The anxieties surrounding security may just warrant a radical rethink about its necessity on production environments.
ASUS: A Risky Integration
It’s clear that ASUS’s recent trend towards deeper software integration within their hardware has backfired. By allowing marketing considerations around flashy features like RGB controls to dictate kernel-level design, the company has inadvertently created a significant vulnerability. Armoury Crate has transformed from mere software to a comprehensive control hub for firmware management and peripheral performance, all while expanding its attack surface exponentially.
Conclusion: Rethinking Trust
ASUS’s Armoury Crate presents a glaring example of how sound security architecture can be neglected in the pursuit of functionality and aesthetic appeal. The broader lesson here is that while hardware manufacturers are eager to supply catchy software solutions, they must equally prioritize robust security to prevent their creations from becoming vehicles for malware and exploitation. For now, consider if the dazzling lights are worth the risk. If you’re unsure about the software’s safety, it may be best to uninstall it entirely and seek alternatives that prioritize security alongside functionality.

Writes about personal finance, side hustles, gadgets, and tech innovation.
Bio: Priya specializes in making complex financial and tech topics easy to digest, with experience in fintech and consumer reviews.